Exam-box shares online exam exercise questions all year round! CompTIA Security+ SY0-501 exam
“CompTIA Security+ Certification Exam” https://www.geekcert.com/sy0-501.html (600 Q&As). Continue to study and we provide an updated cisco SY0-501 exam practice questions and answers. You can practice the test online!
Want to easily handle CompTIA Security+ SY0-501 exam questions: https://www.quora.com/topic/SY0-501-Exam-Questions
Table of Contents:
- Latest CompTIA Security+ SY0-501 pdf
- Test your CompTIA Security+ SY0-501 exam level
- Watch the CompTIA Security+ SY0-501 video tutorial online
- Related SY0-501 Popular Exam resources
- Get Geekcert Coupons (12% OFF)
- What are the advantages of Lead4pass?
Latest CompTIA Security+ SY0-501 pdf
[PDF] Free CompTIA Security+ SY0-501 pdf dumps download from Google Drive: https://drive.google.com/open?id=1p48tIE7GSKFz_V895mWkWk7kaYHYEx0O
CompTIA Security+ Certification – CompTIA IT Certifications: https://certification.comptia.org/certifications/security
CompTIA Security+ SY0-501 Study Guide: https://certification.comptia.org/training/books/security-sy0-501-study-guide
CompTIA Security+ SY0-501 Exam Practice Questions
Success requires effort: https://www.reddit.com/r/CompTIA/comments/cz9qqs/security_501_passed/
QUESTION 1
Which of the following types of keys is found in a key escrow?
A. Public
B. Private
C. Shared
D. Session
Correct Answer: B
https://www.professormesser.com/security-plus/sy0-401/key-escrow-3/
QUESTION 2
An employee uses RDP to connect back to the office network.
If RDP is misconfigured, which of the following security exposures would this lead to?
A. A virus on the administrator\\’s desktop would be able to sniff the administrator\\’s username and password.
B. Result in an attacker being able to phish the employee\\’s username and password.
C. A social engineering attack could occur, resulting in the employee\\’s password being extracted.
D. A man in the middle attack could occur, resulting the employee\\’s username and password being captured.
Correct Answer: D
QUESTION 3
Ann, a user, states that her machine has been behaving erratically over the past week. She has experienced slowness
and input lag and found text files that appear to contain pieces of her emails or online conversations with coworkers.
The
technician runs a standard virus scan but detects nothing.
Which of the following types of malware has infected the machine?
A. Ransomware
B. Rootkit
C. Backdoor
D. Keylogger
Correct Answer: D
QUESTION 4
A security analyst is diagnosing an incident in which a system was compromised from an external IP address. The
socket identified on the firewall was traced to 207.46.130.0:6666. Which of the following should the security analyst do
to determine if the compromised system still has an active connection?
A. tracert
B. netstat
C. ping
D. nslookup
Correct Answer: B
QUESTION 5
A Chief Information Officer (CIO) has decided it is not cost effective to implement safeguards against a known
vulnerability. Which of the following risk responses does this BEST describe?
A. Transference
B. Avoidance
C. Mitigation
D. Acceptance
Correct Answer: D
QUESTION 6
A security analyst has received the following alert snippet from the HIDS appliance: 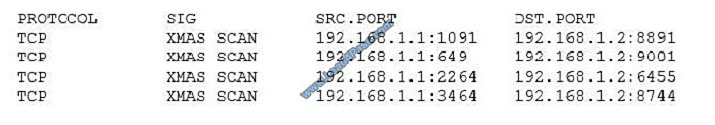
Given the above logs, which of the following is the cause of the attack?
A. The TCP ports on destination are all open
B. FIN, URG, and PSH flags are set in the packet header
C. TCP MSS is configured improperly
D. There is improper Layer 2 segmentation
Correct Answer: B
QUESTION 7
A security engineer is configuring a wireless network with EAP-TLS. Which of the following activities is a requirement for
this configuration?
A. Setting up a TACACS+ server
B. Configuring federation between authentication servers
C. Enabling TOTP
D. Deploying certificates to endpoint devices
Correct Answer: D
QUESTION 8
Joe a computer forensic technician responds to an active compromise of a database server. Joe first collects
information in memory, then collects network traffic and finally conducts an image of the hard drive.
Which of the following procedures did Joe follow?
A. Order of volatility
B. Chain of custody
C. Recovery procedure
D. Incident isolation
Correct Answer: A
QUESTION 9
A Chief Information Officer (CIO) drafts an agreement between the organization and its employees. The agreement
outlines ramifications for releasing information without consent and/or approvals. Which of the following BEST describes
this type of agreement?
A. ISA
B. NDA
C. MOU
D. SLA
Correct Answer: B
QUESTION 10
An administrator intends to configure an IPSec solution that provides ESP with integrity protection, but not confidentiality
protection. Which of the following AES modes of operation would meet this integrity-only requirement?
A. HMAC
B. PCBC
C. CBC
D. GCM
E. CFB
Correct Answer: A
QUESTION 11
Which of the following is the main difference an XSS vulnerability and a CSRF vulnerability?
A. XSS needs the attacker to be authenticated to the trusted server.
B. XSS does not need the victim to be authenticated to the trusted server.
C. CSRF needs the victim to be authenticated to the trusted server.
D. CSRF does not need the victim to be authenticated to the trusted server.
E. CSRF does not need the attacker to be authenticated to the trusted server.
Correct Answer: BC
QUESTION 12
As part of a new industry regulation, companies are required to utilize secure, standardized OS settings. A technical
must ensure the OS settings are hardened. Which of the following is the BEST way to do this?
A. Use a vulnerability scanner.
B. Use a configuration compliance scanner.
C. Use a passive, in-line scanner.
D. Use a protocol analyzer.
Correct Answer: B
QUESTION 13
A Security Officer on a military base needs to encrypt several smart phones that will be going into the field.
Which of the following encryption solutions should be deployed in this situation?
A. Elliptic curve
B. One-time pad
C. 3DES
D. AES-256
Correct Answer: D
Watch the CompTIA Security+ SY0-501 video tutorial online
We offer more ways to make it easier for everyone to learn, and YouTube is the best tool in the video.
Follow channels: https://www.youtube.com/channel/UCXg-xz6fddo6wo1Or9eHdIQ/videos get more useful exam content.
Related SY0-501 Popular Exam resources
| title | youtube | CompTIA | lead4pass | Geekcert Total Questions | |
|---|---|---|---|---|---|
| CompTIA Security+ | lead4pass SY0-501 dumps pdf | lead4pass SY0-501 youtube | CompTIA Security+ SY0-501 Study Guide | https://www.geekcert.com/sy0-501.html | 600 Q&A |
Get Geekcert Coupons(12% OFF)

What are the advantages of Lead4pass?
We have a number of CompTIA, CompTIA, IBM, CompTIA, and other exam experts. We update exam data throughout the year. Top exam pass rate! We have a large user base. We are an industry leader! Choose Geekcert to pass the exam with ease!

Summarize:
The free CompTIA Security+ SY0-501 exam dumps can help you improve your skills and exam experience! To pass the cisco SY0-501 exam at once: https://www.geekcert.com/sy0-501.html
We make CompTIA SY0-501 videos and SY0-501 pdf for you to learn! I hope you can pass the exam easily.