
Geekcert is giving away a free copy of CCNP 350-401 exam questions and answers to welcome Christmas.
15 Free CCNP 350-401 Exam Questions and Answers are the latest exam questions that really help you understand the actual exam situation and help you improve.
Not only that, Geekcert 350-401 exam questions and answers contain 944 questions, which we collectively call “350-401 dumps“: https://www.geekcert.com/350-401.html (PDF+VCE) when you are ready to take practice a few days before the exam All Geekcert 350-401 dumps ensure you actually pass the exam.
Come and enjoy this free Christmas gift (CCNP 350-401 Exam Questions and Answers):
Question 1:
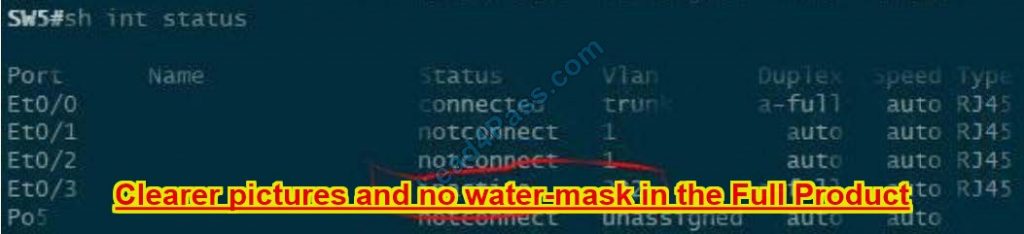
Refer to the exhibit. What happens to access interfaces where VLAN 222 is assigned?

A. STP BPDU guard is enabled
B. A description “RSPAN” is added
C. They are placed into an inactive state
D. They cannot provide PoE
Correct Answer: C
Exam C
Question 2:
Refer to the exhibit.
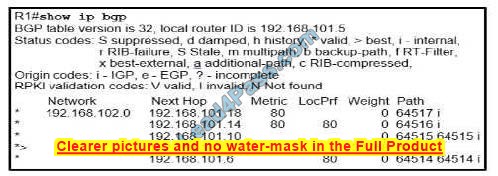
Which IP address becomes the active next hop for 192.168.102 0/24 when 192.168.101.2 fails?
A. 192.168.101.18
B. 192.168.101.6
C. 192.168.101.10
D. 192.168.101.14
Correct Answer: A
The `>\’ shown in the output above indicates that the path with the next hop of 192.168.101.2 is the current best path. Path Selection Attributes: Weight > Local Preference > Originate > AS Path > Origin > MED > External > IGP Cost > eBGP Peering > Router ID BGP prefers the path with the highest weight but the weights here are all 0 (which indicates all routes that are not originated by the local router) so we need to check the Local Preference.
Answer \’192.168.101.18\’ path without LOCAL_PREF (LocPrf column) means it has the default value of 100. Therefore we can find the two next best paths with the next hop of 192.168.101.18 and
192.168.101.10. We have to move to the next path selection attribute: Originate. BGP prefers the path that the local router originated (which is indicated with the “next hop 0.0.0.0”). But none of the two best paths is self-originated. The AS Path of the next hop 192.168.101.18 is shorter than the AS Path of the next hop
192.168.101.10 then the next hop 192.168.101.18 will be chosen as the next best path.
Question 3:
Refer to the exhibit.
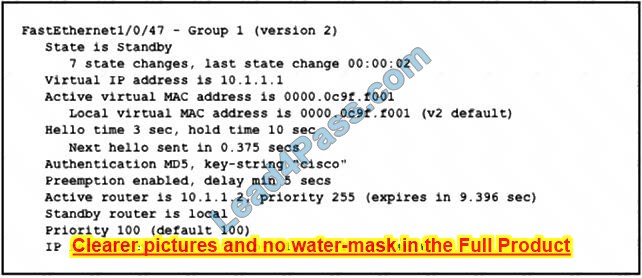
An engineer configures HSRP and enters the show standby command. Which two facts about the network environment are derived from the output? (Choose two.)
A. The local device has a higher priority selling than the active router
B. The virtual IP address of the HSRP group is 10.1.1.1.
C. If the local device fails to receive a hello from the active router for more than 5 seconds, it becomes the active router.
D. The hello and hold timers are set to custom values.
E. If a router with a higher IP address and the same HSRP priority as the active router becomes available, that router becomes the new active router 5 seconds later.
Correct Answer: BE
Question 4:
An engineer must enable a login authentication method that allows a user to log in by using local authentication if all other defined authentication methods fail Which configuration should be applied?
A. aaa authentication login CONSOLE group radius local-case enable aaa
B. authentication login CONSOLE group radius local enable none
C. aaa authentication login CONSOLE group radius local enable
D. aaa authentication login CONSOLE group tacacs+ local enable
Correct Answer: D
Question 5:
In a traditional 3-tier topology, an engineer must explicitly configure a switch as the root bridge and exclude it from any further election process for the spanning-tree domain. Which action accomplishes this task?
A. Configure the spanning-tree priority to 32768
B. Configure root guard and portfast on all access switch ports.
C. Configure BPDU guard in all switch-to-switch connections.
D. Configure the spanning-tree priority equal to 0.
Correct Answer: B
The root guard does not allow the port to become an STP root port, so the port is always STP-designated. If a better BPDU arrives on this port, the root guard does not take the BPDU into account and elects a new STP root. Instead, the root guard puts the port into the root-inconsistent STP state which is equal to a listening state. No traffic is forwarded across this port.
Reference: http://www.cisco.com/c/en/us/support/docs/lan-switching/spanning-tree-protocol/10588-74.html
Question 6:
With IGMPv2, which multicast group address does the IGMP querier use to send query messages to all hosts on the LAN?
A. 239.0.0.2
B. 224.0.0.1
C. 239.0.0.1
D. 224.0.0.2
Correct Answer: B
Question 7:
By default, which virtual MAC address does HSRP group 15 use?
A. 05:5e:ac:07:0c:0f
B. c0:42:34:03:73:0f
C. 00:00:0c:07:ac:0f
D. 05:af:1c:0f:ac:15
Correct Answer: C
Question 8:
On which protocol or technology is the fabric data plane based in Cisco SD-Access fabric?
A. LISP
B. IS-IS
C. Cisco TrustSec
D. VXLAN
Correct Answer: D
The tunneling technology used for the fabric data plane is based on Virtual Extensible LAN (VXLAN). VXLAN encapsulation is UDP based, meaning that it can be forwarded by any IP-based network (legacy or third party) and creates the overlay network for the SD-Access fabric. Although LISP is the control plane for the SD-Access fabric, it does not use LISP data encapsulation for the data plane; instead, it uses VXLAN encapsulation because it is capable of encapsulating the original Ethernet header to perform MACin-IP encapsulation, while LISP does not. Using VXLAN allows the SD-Access fabric to support Layer 2 and Layer 3 virtual topologies (overlays) and the ability to operate over any IP-based network with built-in network segmentation (VRF instance/VN) and built-in group-based policy. Reference: CCNP and CCIE Enterprise Core ENCOR 350-401 Official Cert Guide
Question 9:
DRAG DROP
Drag and drop the characteristics from the left onto the orchestration tools they describe on the right.
Select and Place:
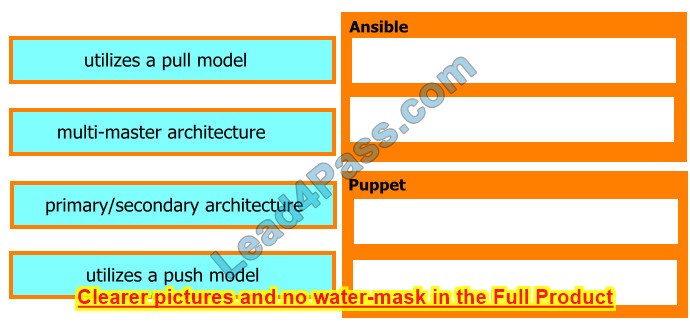
Correct Answer:
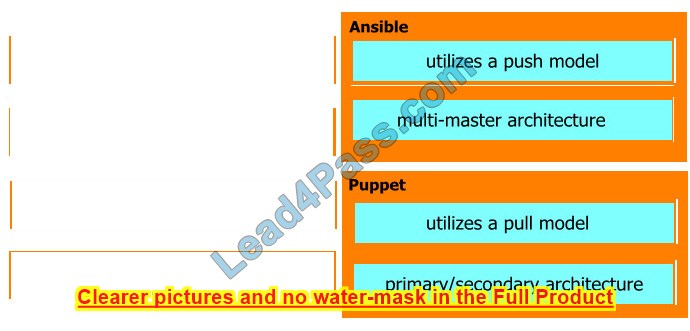
Ansible runs with a single active node, called the Primary instance. If the primary goes down, there is a Secondary instance to take its place. Puppet has multi-master architecture. If the active master goes down, then the other master takes the active master’s place. https://www.javatpoint.com/ansible-vs-puppet
Question 10:
What mechanism does PIM use to forward multicast traffic?
A. PIM sparse mode uses a pull model to deliver multicast traffic.
B. PIM dense mode uses a pull model to deliver multicast traffic.
C. PIM sparse mode uses receivers to register with the RP.
D. PIM sparse mode uses a flood and prune model to deliver multicast traffic.
Correct Answer: A
PIM dense mode (PIM-DM) uses a push model to flood multicast traffic to every corner of the network. This push model is a brute-force method of delivering data to the receivers. This method would be efficient in certain deployments in which there are active receivers on every subnet in the network. PIM-DM initially floods multicast traffic throughout the network.
Routers that have no downstream neighbors prune the unwanted traffic. This process repeats every 3 minutes. PIM Sparse Mode (PIM-SM) uses a pull model to deliver multicast traffic. Only network segments with active receivers that have explicitly requested the data receive the traffic. PIM-SM distributes information about active sources by forwarding data packets on the shared tree.
Because PIM-SM uses shared trees (at least initially), it requires the use of an RP. The RP must be administratively configured in the network. Answer C seems to be correct but it is not, PIM spare mode uses sources (not receivers) to register with the RP.
Sources register with the RP, and then data is forwarded down the shared tree to the receivers. Reference: Selecting MPLS VPN Services Book, page 193
Question 11:
What is the recommended MTU size for a Cisco SD-Access Fabric?
A. 1500
B. 9100
C. 4464
D. 17914
Correct Answer: B
VXLAN adds 50 bytes to the original packet. The common denominator and recommended MTU value available on devices operating in a fabric role is 9100.
The network should have a minimum starting MTU of at least 1550 bytes to support the fabric overlay. MTU values between 1550 and 9100 are supported along with MTU values larger than 9100 though there may be additional configuration and limitations based on the original packet size.
MTU 9100 is provisioned as part of LAN Automation. Devices in the same routing domain and Layer 2 domain should be configured with a consistent MTU size to support routing protocol adjacencies and packet forwarding without fragmentation.
Question 12:
Which two statements about AAA authentication are true? (Choose two)
A. RADIUS authentication queries the router`s local username database
B. TACACS+ authentication uses an RSA server to authenticate users
C. Local user names are case-insensitive
D. Local authentication is maintained on the router
E. KRB5 authentication disables user access when an incorrect password is entered
Correct Answer: DE
Question 13:
Refer to the exhibit. Reachability between servers in a network deployed with DHCPv6 is unstable. Which command must be removed from the configuration to make DHCPv6 function?

A. ipv6 address 2001:0:1:4::1/64
B. ipv6 DHCP server DHCPPOOL
C. ipv6 nd ra suppress
D. address prefix 2001:0:1:4::/64 lifetime infinite infinite
Correct Answer: C
Question 14:
What is a characteristic of MACsec?
A. 802.1AE provides encryption and authentication services
B. 802.1AE is bult between the host and switch using the MKA protocol, which negotiates encryption keys based on the master session key from a successful 802 1X session
C. 802.1AE is bult between the host and switch using the MKA protocol using keys generated via the Diffie-Hellman algorithm (anonymous encryption mode)
D. 802.1AE is negotiated using Cisco AnyConnect NAM and the SAP protocol
Correct Answer: B
MACsec, defined in 802.1AE, provides MAC-layer encryption over wired networks by using out-of-band methods for encryption keying. The MACsec Key Agreement (MKA) Protocol provides the required session keys and manages the required encryption keys. MKA and MACsec are implemented after successful authentication using the 802.1x Extensible Authentication Protocol (EAP-TLS) or Pre Shared Key (PSK) framework.
Question 15:
Which two statements about IP SLA are true? (Choose two)
A. It uses NetFlow for passive traffic monitoring
B. It can measure MOS
C. The IP SLA responder is a component in the source Cisco device
D. It is Layer 2 transport-independent correct
E. It uses active traffic monitoring correct
F. SNMP access is not supported
Correct Answer: DE
IP SLAs allows Cisco customers to analyze IP service levels for IP applications and services, to increase productivity, lower operational costs, and reduce the frequency of network outages. IP SLAs use active traffic monitoringhe generation of traffic in a continuous, reliable, and predictable manneror measuring network performance. Being Layer-2 transport independent, IP SLAs can be configured end-toend over disparate networks to best reflect the metrics that an end-user is likely to experience.
…
Take advantage of this Christmas gift to help you really understand the CCNP 350-401 certification exam, download 350-401 dumps: https://www.geekcert.com/350-401.html, use PDF and VCE tools to help you speed up your study progress and really Successfully pass the CCNP 350-401 certification exam.